Bitcoin Is An Idea
Don’t worry about people stealing an idea. If it’s original, you will have to ram it down their throats.
Howard H. Aiken
There’s no flesh or blood within this cloak to kill. There’s only an idea. Ideas are bulletproof.
Alan Moore, V for Vendetta
On October 31st, 2008, the future trajectory of our global society was forever changed. A breakthrough was made, and an unstoppable idea was let loose on the world. An idea so profound, so outrageous, that it was ignored by almost everyone for the first couple of years—and is still dismissed by most: Bitcoin: A Peer-to-Peer Electronic Cash System.
The whitepaper released by Satoshi Nakamoto on this Halloween night describes an idea that will inevitably take the world by storm. While most people still think of Bitcoin as nothing more than a get-rich-quick scheme — completely missing the profound change it will continue to have on society — it becomes more obvious every day that it won’t go away.
“Ideas, unlike solid structures, do not perish,” Alan Moore reminds us. “They remain immortal, immaterial and everywhere, like all Divine things.”
On this fateful night in 2008, Satoshi let the genie out of the bottle. We went from a world where digital cash was just an idea to a world where Bitcoin exists. Not only is the idea here to stay, but with every passing block, Bitcoin reminds us that this idea is now a reality. As we shall see, this new reality is more powerful than one might think at first. It is powerful because it will usher in a new economic paradigm. It is powerful because the time is ripe for it. It is powerful because it can’t be stopped. As Victor Hugo reminds us: nothing is as powerful as an idea whose time has come. Bitcoin is here to stay; and Bitcoin’s time is now.
An Idea Whose Time Has Come
One withstands the invasion of armies; one does not withstand the invasion of ideas.
Victor Hugo
Contrary to popular belief, Bitcoin did not come out of nowhere. The idea of digital cash has a long and rich history. Most notably, a loose collective known as the cypherpunks wrote at length about digital anonymous cash, how such systems might be realized, and the societal implications of strong cryptography in general. Hence the name: cypherpunks. 1
After forming the group in 1992, Eric Hughes, Timothy C. May, and John Gilmore created the cypherpunk mailing list to discuss and share their ideas around cryptography, remailers, anonymity, digital cash, and “other interesting things” with a wider group of people. Many years later, a cypherpunk by the name of Satoshi Nakamoto chose to publish the Bitcoin whitepaper on a similar mailing list: the cryptography mailing list.
As is apparent by studying their writings, the cypherpunks cared a great deal about the idea of digital cash. In 1993, Eric Hughes discussed the idea of digital cash, its relation to privacy, and its importance for a free society in A Cypherpunk’s Manifesto: “Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am.”
The idea of digital cash (or electronic cash, as Satoshi chose to call it in the Bitcoin whitepaper) is to have something in the digital realm which behaves as cash does in the real world. No identity or sign-up required, directly exchangeable for goods and services, and virtually untraceable.
Even the IANA2, a standards organization responsible for defining HTTP status codes (among other things), recognizes the idea of digital cash. We all know the infamous 404 error code, indicating that a resource can’t be found. Few people know that there is also a 402 error code, indicating that the resource can’t be accessed because it requires payment. However, since digital cash did not exist at the time, the status code was “reserved for future use” and isn’t widely used as of today.
The cypherpunks focused mainly on the privacy aspect of digital cash. Monetary and economic aspects were secondary. They realized that privacy is absolutely paramount for a free and open society. After all, the opposite—complete surveillance—can only lead to oppression and stagnation, since new and controversial ideas won’t be allowed to flourish. No matter what freedoms you think you have, in the end, surveillance renders all other freedoms useless.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Eric Hughes, A Cypherpunk’s Manifesto
While Bitcoin is a breakthrough in many ways, all the technical parts that make it work did exist already:
- Public-key cryptography
- Peer-to-peer networks
- Digital signatures
- Cryptographic hash functions
- Cryptographic time stamps
- Hash chains
- Proof-of-work
We will explore all these concepts in more detail at later points in the book.
Satoshi did not invent any clever new algorithm or cryptographic primitive. Instead, he found a way to combine existing technologies in an ingenious way, using economic incentives and game theory to bootstrap and secure the system.
The cypherpunks were well aware that even if the base technology exists in theory, some things simply need time to develop. In 1992, Timothy May wrote in The Crypto Anarchist Manifesto: “The technology for this [...] has existed in theory for the past decade. [...] But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable.”3
While I do believe that Bitcoin (the network) is essentially unstoppable already, Bitcoin the idea is truly unstoppable. After all, as Alan Moore put it so succinctly, ideas are bulletproof.
In the first decade of its existence, Bitcoin went from idea to implementation to proof-of-concept to niche monetary asset. In the next decade, it will probably become a force on its own, transcending boundaries and transforming our understanding of money and value in the process. The idea, however, wasn’t conceived at Bitcoin’s birth: it was conceived by thinkers and tinkerers of the electronic age, multiple decades before Satoshi Nakamoto entered the scene.
History of Digital Cash
A lot of people automatically dismiss e-currency as a lost cause because of all the companies that failed since the 1990’s.
Satoshi Nakamoto
Bitcoin’s pre-history is as long as it is fascinating. Satoshi was able to build upon various technologies and protocols, some of which go back 50 years and more. While 50 years might be a long time in technology, the art of cryptography is way more ancient than that, dating back as far as 1900 BC.
It’s hard to say what the most important building blocks were, but the most fundamental ones are probably digital signatures4 (Diffie and Hellman, 1976) and public-key cryptography5 (Rivest, Shamir, Adleman, 1978). Without these ideas, Bitcoin couldn’t exist.
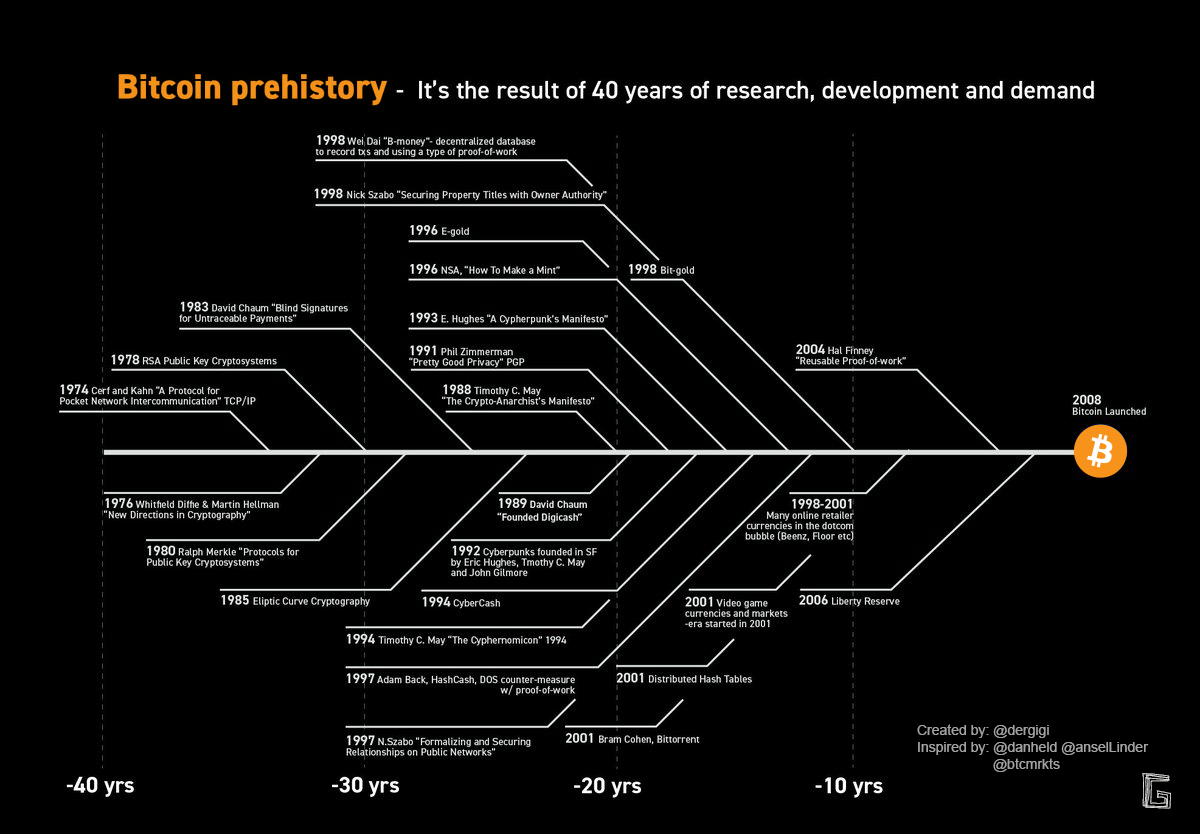
Various digital cash systems have been developed before Bitcoin. All of them failed eventually, and all for similar reasons. The following are particularly interesting in the context of Bitcoin:
- Ecash by David Chaum (1982)
- E-gold by Douglas Jackson and Barry Downey (1996)
- hashcash by Adam Back (1997)
- bit gold by Nick Szabo (1998)
- b-money by Wei Dai (1998)
- RPOW—Reusable Proofs of Work by Hal Finney (2004)
Let’s take a closer look at these systems, see what they brought to the table, and explore why they failed.
Ecash (David Chaum, 1982)
Ecash utilized digital signatures to prove ownership, an idea that is still used in Bitcoin today. Proposed by David Chaum in 1982, it was later implemented by his company and operational for three years before the firm went bankrupt in 1998. Chaum is still active as a cryptographer. He pioneered many cryptographic techniques and pushed the development of privacy-preserving technologies forward. One of the privacy-enhancing transaction techniques in Bitcoin, the Chaumian CoinJoin, is named in his honor. While Ecash was cryptographically and technologically interesting, it wasn’t a monetary innovation and ultimately failed because it was operated by a centralized entity: DigiCash Inc., the company founded by Chaum.
E-gold (Douglas Jackson and Barry Downey, 1996)
E-gold wasn’t particularly ground-breaking cryptographically, but it was one of the first digital currencies that gained traction. Although others existed before it (OS-Gold, Standard Reserve, INTGold), e-gold is considered to be the first successful digital currency that became popular enough to have some merchant adoption. At its height, e-gold had five million users and processed value transfers in the order of $2 billion. Besides the e-gold tokens backed by gold, other precious e-metals could be acquired: e-silver, e-platinum, and e-palladium. The demise of e-cash, again, was that it was a centralized service run by a company: Gold & Silver Reserve Inc. The U.S. government filed a lawsuit claiming that the company was running an unlicensed money transmitting business. In the end, the e-cash project failed because it was operated by a company that could be shut down.
Hashcash (Adam Back, 1997)
Originally proposed in 1997, and more formally published as Hashcash - A Denial of Service Counter-Measure in 2002, Hashcash is one of the essential ideas that made Bitcoin possible. While other researchers had the idea of Pricing via Processing6 before Adam Back (Dwork and Naor, 1992), his paper was referenced by Satoshi in the Bitcoin whitepaper and led to what is known as Bitcoin’s proof-of-work today. As far as I can tell, the term proof-of-work was first introduced in the Hashcash paper.7
Hal Finney, one of the legends of the early Bitcoin days, beautifully and succinctly described hashcash as follows: “Hashcash is a textual string in a particular format which has a special property: when run through the SHA-1 hash algorithm the result has the first N of its initial bits equal to zero, where N is typically around 20-30. The terminology used for hashcash describes the number of leading zero bits as the size of its ‘collision’. Because of SHA-1’s properties, the only way to find a string with a large collision size is by exhaustive search: trying one variation after another, until you get lucky.”8
For example, the SHA1 hash of the hashcash string
1:20:040806:foo::65f460d0726f420d:13a6b8
produces a string with five leading zeros: 9
00000f91d51a9c213f9b7420c35c62b5e818c23e
The leading number of zeros in a hashed hashcash string indicates how valuable the hashcash string is. Because there is no other way than brute force, the number of zeros is directly correlated with the cost of production, which, in the digital realm, is the cost of computation.
In essence, hashcash utilizes the fact that computation cycles cost time and real-world resources. Back proposed that introducing the electronic equivalent of a postage stamp via hashcash could be its main use case. While fighting e-mail spam seemed to be on the top of his mind, he also proposed that it could be used as digital cash, going as far as sketching out a migration path that could lead to its integration in Chaum’s ecash. While Bitcoin’s proof-of-work algorithm differs slightly from Hashcash’s (using double-SHA256 instead of SHA1, for example)—the idea remains the same: computing a hash can’t be done without flipping bits, which in turn can’t be done without expending time and energy. Hashcash exploits the peculiar property of our universe that any computation, i.e. any change of a system, requires energy. In other words: you can’t cheat physics. Computation will never be free.
The genius of Hashcash was finding and describing computational functions where computation is expensive but verification is inexpensive. You can think of hashcash puzzles like solving Sudokus or Rubik’s Cubes: hard to solve, easy to check. While various Hashcash implementations were used to prevent spam, the concept wasn’t widely applied to currencies before Satoshi used it in Bitcoin.
Bit gold (Nick Szabo, 1998)
Building upon the work of Adam Back and Hal Finney, “bit gold” can be described as a direct predecessor to “bit coin.”10 While the system was never implemented, the way Szabo envisioned it to work in theory is remarkably close to the way Bitcoin works in actuality.
The purpose of bit gold, as the name implies, was to create a digital monetary good independent from any central authority, which in turn can be used as a store of value—just like gold in the physical world. Szabo writes: “The objective, which I argued for vigorously, was to create a long term store of value independent of any central authority, yet far more secure than traditional gold.” 11
Precious metals and collectibles12 have an unforgeable scarcity due to the costliness of their creation. [...] Thus, it would be very nice if there were a protocol whereby unforgeably costly bits could be created online with minimal dependence on trusted third parties, and then securely stored, transferred, and assayed with similar minimal trust.
One point that Szabo makes repeatedly is that physical gold has various problems and is quite insecure when compared to solutions rooted in cryptography. Storage, for example, is only as secure as the doors and walls that protect it. And in the end, someone can always break in and take it. The same goes for transportation. You can’t send it securely without extraordinary effort—and no matter your effort, someone could always intercept it. Even validation is problematic, as an abundance of “gold” bars made predominantly of lead or tungsten attest. Over time, these insufficiencies of gold inevitably lead to centralization in vaults and banks, which comes with its own set of problems.
Bit gold achieves all the essential properties of gold, while avoiding the insecurity of gold which has plagued civilization for millenia.
The intended purpose of bit gold isn’t the only thing that will be familiar to bitcoiners today. The way the system was supposed to work will be familiar as well. Granted, there are some crucial differences, but the basic idea is eerily similar.
The following seven steps are taken directly from the bit gold paper and outline how the system would operate:
- A public string of bits, the “challenge string,” is created (see step 5).
- Alice on her computer generates the proof of work string from the challenge bits using a benchmark function.
- The proof of work is securely timestamped. This should work in a distributed fashion, with several different timestamp services so that no particular timestamp service need be substantially relied on.
- Alice adds the challenge string and the timestamped proof-of-work string to a distributed property title registry for bit gold. Here, too, no single server is substantially relied on to properly operate the registry.
- The last-created string of bit gold provides the challenge bits for the next-created string.
- To verify that Alice is the owner of a particular string of bit gold, Bob checks the unforgeable chain of title in the bit gold title registry.
- To assay the value of a string of bit gold, Bob checks and verifies the challenge bits, the proof of work string, and the timestamp.
There are two crucial differences between Szabo’s approach and Bitcoin. The first is that bit gold requires two separate registries: one for recording timestamps (to note when the bit gold was created), and one for recording property titles (to see who is owning the bit gold). The second is that bit gold is supposed to rely on benchmark functions (as opposed to one-way functions) to generate a proof of work. Benchmark functions are functions proposed by Szabo that are computationally stable, i.e. a set of functions that maintain a similar degree of difficulty among all miners. He put considerable effort into defining and exploring these functions, trying to formulate mathematical proofs that every computation will take at least a certain amount of time no matter what computer architecture is used.13 However, since computers get faster all the time, he remarked that finding such a function will be difficult: “A potential big problem remains: [...] The world lacks a cryptanalytically stable problem.”
The lack of a stable benchmark function leads to a multitude of problems: older “coins” created by users would have a different costliness than newer ones since computers get faster as technology progresses. Thus, two different coins—or strings of bit gold, as Szabo called them—would not have the same value. If Moore’s Law is any indication, a coin that is two years older than another one might be considered twice as valuable because the doubling of processing power made minting the newer one twice as easy. Another problem is that—if bit gold became valuable enough—computational breakthroughs might be kept secret by those who made them, so valid strings of bit gold can be amassed and sold on the market at a premium. This would exacerbate the inflation problem, which is another problem that Szabo identified but didn’t solve.
In addition, Szabo correctly identified the issues of previous approaches such as Hashcash and MicroMint14: (1) their value was dependent on a central authority, (2) the hash functions they use are cryptographically vulnerable, i.e. they lack cryptanalytical stability. As described above, the later problem is still present in bit gold.
b-money (Wei Dai, 1998)
Like Szabo’s bit gold, Wei Dai’s b-money was never implemented. It remained a theoretical proposal of how a monetary protocol could work. While Bitcoin is a working implementation of the vision that b-money outlines, it seems that Satoshi was unaware of b-money while coming up with the core design of Bitcoin. As Wei Dai wrote in a response to a LessWrong article: “my understanding is that the creator of Bitcoin [...] didn’t even read my article before reinventing the idea himself. He learned about it afterward and credited me in his paper. So my connection with the project is quite limited.” In 2013, Adam Back commented on this, mentioning that he introduced Satoshi to Wei Dai’s b-money after Satoshi reached out to him.
In his proposal, Dai is very outspoken regarding the motivation of his system. Citing Tim May’s ideas around crypto-anarchy, he writes that “in a crypto-anarchy the government is not temporarily destroyed but permanently forbidden and permanently unnecessary. It’s a community where the threat of violence is impotent because violence is impossible, and violence is impossible because its participants cannot be linked to their true names or physical locations.”
Dai goes on to describe a system where every participant maintains a separate database of how much money belongs to each user. Users are identified by pseudonyms (public keys), monetary units are created in relation to computational effort, money is transferred by signing messages, and contracts are executed by the protocol automatically. Describing—in spirit, but not in detail—how Bitcoin operates today.
He outlines five things that are necessary for such a system to function:
- The creation of money
- The transfer of money
- The effecting of contracts
- The conclusion of contracts
- The enforcement of contracts
While b-money solves many of the problems that are inherent to electronic money, the problem described by Szabo in bit gold remains. Dai mentions this in his proposal as follows: “One of the more problematic parts in the b-money protocol is money creation. This part of the protocol requires that all of the account keepers decide and agree on the cost of particular computations. Unfortunately because computing technology tends to advance rapidly and not always publicly, this information may be unavailable, inaccurate, or outdated, all of which would cause serious problems for the protocol.”
Dai proposes a solution to this problem by describing a sub-protocol that is solely responsible for money creation. Participants would periodically agree upon how much money should be created, collectively working together in a market-driven cycle that consists of four steps: planning, bidding, computation, and creation. Since b-money was never implemented in the form proposed by Dai, it is unclear whether this elaborate money-creation scheme would have worked as intended.
RPOW—Reusable Proofs of Work (Hal Finney, 2004)
As the name suggests, Hal Finney found a way to make the proof-of-work tokens from Adam Back’s hashcash reusable.
Here is how it works, paraphrasing the original announcement by Hal Finney himself: The system receives hashcash as a proof-of-work (POW) token, and in exchange creates RSA-signed tokens which are called reusable proof-of-work (RPOW) tokens. RPOWs can then be transferred from person to person and exchanged for new RPOWs at each step. Each RPOW token can only be used once but since it gives birth to a new one, it is as though the same token can be handed from person to person.
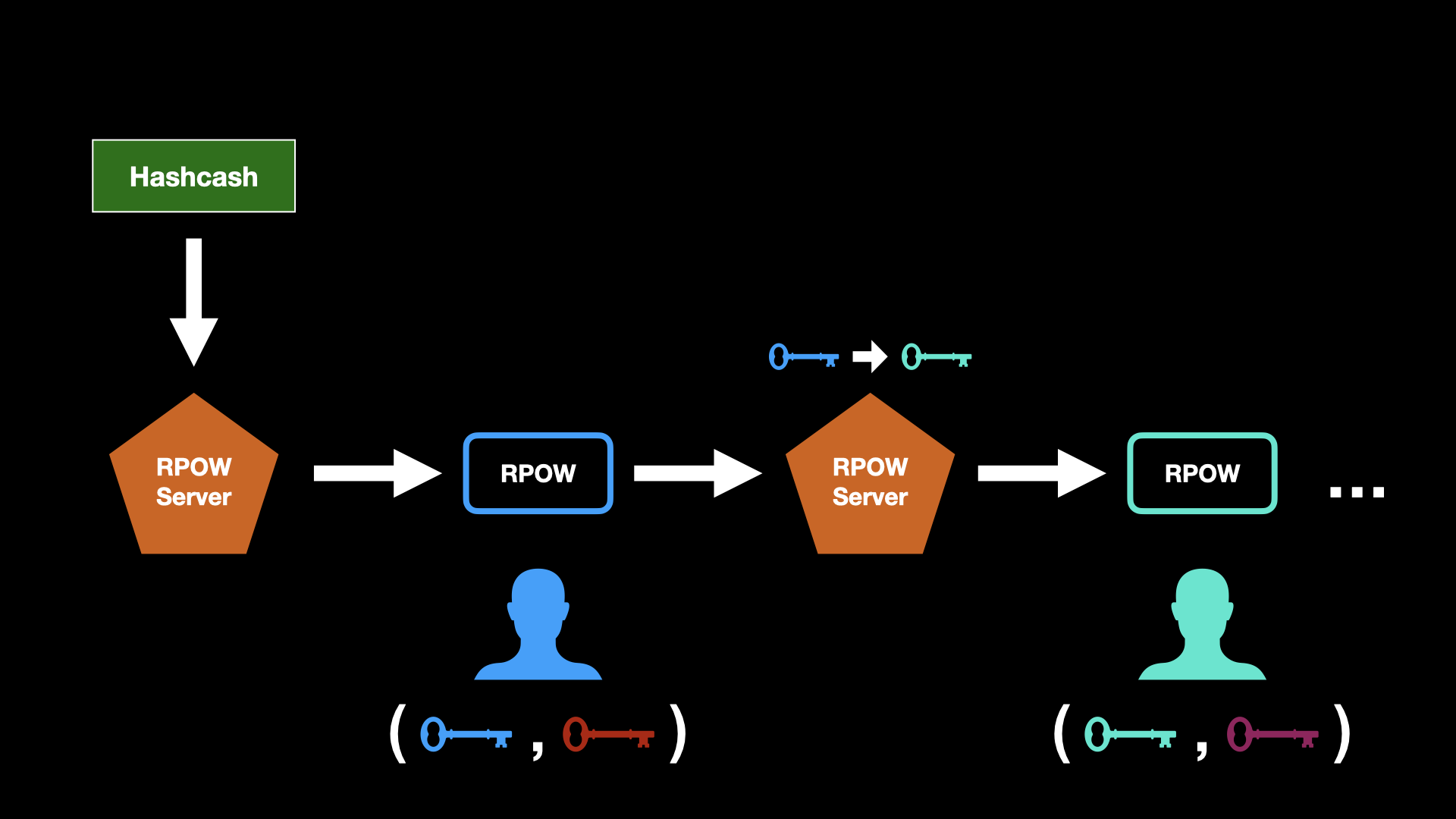
In essence, a user can create RPOW tokens via the RPOW client software, which takes a proof-of-work string as generated by the Hashcash software invented by Adam Back. This string is signed by the user’s private key and subsequently registered by an RPOW server, recording that this token is belonging to the user’s public key. The user can then pass that token on to someone else by signing a “transfer order” to another user’s public key. The server then duly registers the token as belonging to the corresponding private key.
As is apparent by studying his writings, Hal Finney was inspired and building upon work by Nick Szabo, most notably his ideas around “bit gold” and digital collectibles. Discussing possible applications of RPOW, Hal writes: “Security researcher Nick Szabo has coined the term bit gold for information objects which are provably costly to create. He suggests that these could even serve as the foundation for a sort of payment system, playing the role in the informational world of gold in the physical world. RPOW would facilitate the use of POW tokens as a form of bit gold by allowing the tokens to be passed and exchanged from person to person.”15
Hal’s implementation was a practical solution to a problem inherent in proof-of-work tokens, namely that the POW tokens themselves don’t make very good money. POW tokens are just hashes—bits of information—that can be double-spent. With the concept of RPOW servers, Hal introduced central, but trust-minimized authorities that can cryptographically determine a chain of ownership. This allows proof-of-work tokens to be re-used, albeit in a limited, sequential way.
While the RPOW architecture is hierarchical, i.e. its clients rely on specialized servers, the trust users need to have in an RPOW server is minimized. This is possible because the RPOW server software is run on an IBM 4758 secure cryptographic coprocessor, a high-security tamper-resistant PCI board that cryptographically ensures that the software running on the server is the software that was published and audited. This makes any RPOW server a system whose security properties can be analyzed and evaluated by anyone. In other words, an RPOW server is a transparent server, which makes the RPOW system as a whole trust-minimized. Everyone knows the code that makes the system work, as well as the rules that are in place.
We know the source code. We know the rules.
So, what exactly are the rules of the RPOW system? According to its inventor, they are as follows:16
- No inflation
- No back doors
- Privacy protection
The “no inflation” rule has to be understood in terms of the constraints set up by the system itself, i.e. that any RPOW server will only create RPOW tokens equal in value to incoming POW and RPOW tokens. Since users can create new proof-of-work tokens via Adam Back’s hashcash, inflation in terms of new supply coming into the system can and will always happen.
“To enforce the no-inflation rule, the RPOW server must make sure that no POW or RPOW can be used more than once as part of an exchange. Each one is created, and then exchanged at the server for a new RPOW, and after that, the old one can never be used again. The RPOW server enforces this rule primarily by keeping a record of all of the RPOWs and POWs that it has seen in the past. Whenever one is offered for exchange, the RPOW server compares it against this database of previously-seen RPOWs. If it is on the list, this is an attempt to reuse the POW or RPOW, and the exchange request is rejected. If the POW or RPOW is not on the list, it is added to the list, and then the RPOW server will sign the bignum value supplied as part of the exchange, creating a new RPOW.”
The “no back doors” rule refers to the transparency of the system. Everyone can inspect how it works at all times, there are no hidden parts.
The “privacy protection” rule is an interesting one. Hal wrote at length about how privacy is an inherently desirable feature, advocating the use of Tor17 to connect to the RPOW servers and discussing both attack vectors (linkage attacks) and improvements such as the use of blind signatures. In his writings, he goes on to point out two additional things: (1) the “owner is the enemy”, and (2) the “programmer is the enemy”, reminding us that any system that facilitates the trust-minimized exchange of money needs to be set up and operate under an adversarial mindset.
Next to hashcash, RPOW was one of the systems that was actually implemented. However, probably because of the effort required to run RPOW servers, as well as a lack of incentives to do so, Finney’s reusable proof-of-work tokens never gained traction and the project was eventually discontinued.
Satoshi’s Breakthrough
I hope it’s obvious it was only the centrally controlled nature of those systems that doomed them.
On February 11, 2009, Satoshi posted an announcement to the P2P Foundation forums. The P2P Foundation studies the impact of peer-to-peer technology and thought on society, describing itself as “The Foundation for Peer to Peer Alternatives.” Thus, it was a very fitting place to announce the invention of a peer-to-peer money like Bitcoin.
In his announcement, Satoshi describes Bitcoin as a “P2P e-cash system” that has “no central server or trusted parties” because “everything is based on crypto proof instead of trust.”
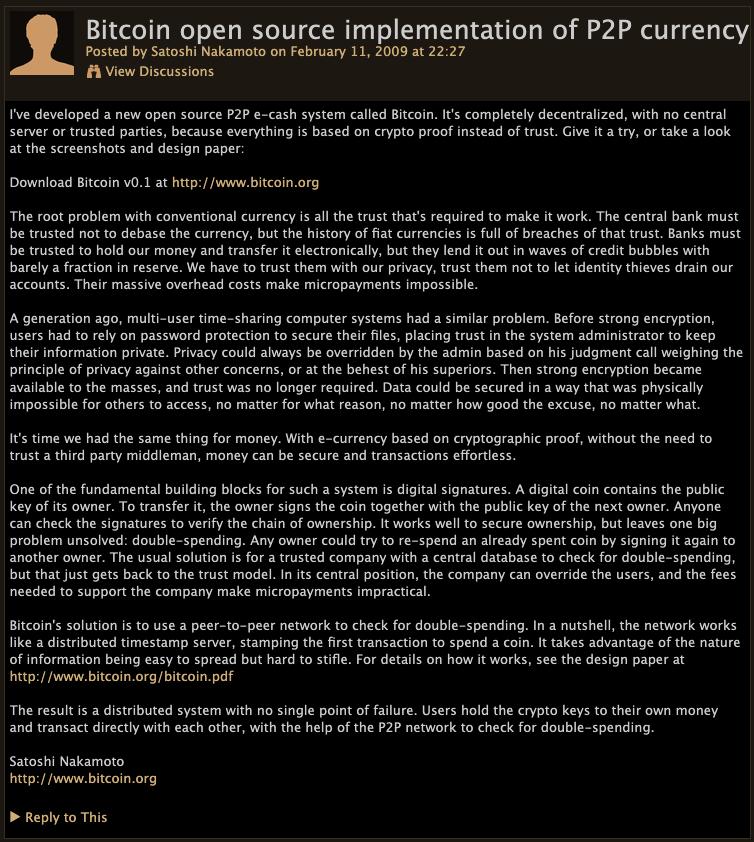
He identifies multiple problems with our current monetary system and the conventional currencies that are native to it:
- trust in third parties
- currency debasement by central banks
- credit bubbles
- fractional reserve banking
- privacy
- lack of micropayments due to overhead costs
- middlemen
Just by glancing at this list, Bitcoin’s enormously ambitious scope becomes apparent. Satoshi didn’t set out to solve one problem. He set out to solve many problems at once. Amazingly, he got so many things right from the start that he was actually able to solve most of them. All he had to do was convince others that his solution actually worked.
Knowing his audience, he goes on to point out how similar trust-related issues were solved in the world of computer systems in general, i.e. how strong cryptography did away with having to trust system administrators with your data. Once your files are encrypted, you do not need to trust whoever has access to these files, since they would need your password to decrypt them. In other words: we moved from trusting humans to trusting mathematics. This is especially relevant in a peer-to-peer setting, because thanks to strong cryptography, you can exchange confidential data with others—including your future self—without having to rely on any middlemen.
It’s time we had the same thing for money.
To better understand Satoshi’s breakthrough, let’s recap what was possible before and where other systems fell short. The following is what was possible before Bitcoin:
- Account creation via public-key cryptography
- Unforgeable costly tokens via proof-of-work
- Proving ownership via digital signatures
- Passing on proof-of-work tokens via signature chains
And here is what wasn’t possible:
- Preventing double-spending without a trusted third party
- Limiting supply without a trusted third party
To Satoshi, it was obvious that any centrally controlled system will get shut down by governments. Thus, the system he wanted to build had one goal above all others: decentralization.
Governments are good at cutting off the heads of centrally controlled networks like Napster, but pure P2P networks like Gnutella and Tor seem to be holding their own.
The above quote beautifully encapsulates why decentralization is so important: there are no heads to cut off, no CEOs to arrest, no leaders to blackmail or pressure, no single group of people to subpoena, no servers to shut down. In other words: decentralization maximizes survival.
A central point in any system makes it vulnerable and thus prone to attack. A sufficiently motivated attacker will find and exploit these points of failure. And when it comes to money, the state has all the motivation in the world to shut down a competing system. This—and only this—is why Bitcoin’s design is so intricate and complicated. Its incentive-driven architecture favors one thing above all else: survival. Because you would have to destroy all parts of it simultaneously, a radically decentralized system is extremely resilient to any kind of disruption.
While previous attempts—especially bit gold, b-money, and RPOW—were quite close to Bitcoin’s eventual design, all systems had at least one of the following flaws:
- Central ownership registry required to prevent double-spending
- Coin value dependent on a central authority
- Controlled issuance only possible through a centralized body
- Unstable proof-of-work function (computationally speaking)
Except for the last point, all of these flaws are flaws because they require a centralized body, exposing a head that could be cut off by governments. Satoshi’s genius was the removal of all heads, including his own.
Again, the essential problem for money in the digital realm boils down to two things: scarcity, and double-spending. While obviously related—you can’t have digital scarcity without solving the problem of double-spending - they aren’t exactly the same thing. Satoshi solved both of these problems at once, by using a peer-to-peer network as a non-central ledger, using a global timechain to synchronize state, and dynamically adjusting the puzzle difficulty to achieve cryptanalytical stability—making a predictable issuance possible.
Further, he combined the process of issuance, transfer, and verification, removing the need for any trusted third party. The genius of Bitcoin is that every node can verify everything for itself at all times. To paraphrase Hal Finney: “You know the source code. You know the rules.”
Satoshi was able to decentralize all the functions of Wei Dai’s b-money (creation and transfer of money; effecting, conclusion, and enforcement of contracts) while also solving the problems of Szabo’s “bit gold” (coin value dependent on a central authority; hash functions lack cryptanalytical stability). He did it by taking Hal Finney’s idea of reusable proof-of-work tokens to the next level, creating a digital asset that is both fungible and has a high unforgeable costliness. Like RPOW before it, the resulting system has no inflation, no back doors, and protects the privacy of its users.
It is helpful to look at the different functions of a financial- or banking-type system to understand why Bitcoin operates in the way it does. In essence, such a system needs to be able to do the following:
- Account Creation: users need to be able to create accounts and authenticate themselves.
- Record Ownership: the system needs to be able to record who owns what.
- Prove Ownership: some sort of certification is required to confirm that a user actually owns the asset, so the user can prove this fact to himself and others.
- Transfer Ownership: users need to be able to transfer ownership of assets.
- Security: the system needs to make sure that ownership records, the computer network, and user data are safe.
In addition, when it comes to monetary systems, it is desirable to have the following:
- Scarcity: the money should be hard to produce, i.e. it should have unforgeable costliness as described by Nick Szabo.
- Controlled Issuance: new monetary units should be issued evenly and over a long period of time, allowing for organic distribution among participants.
- Auditability: independent third parties should be able to audit the supply (as well as the security of the system).
Satoshi found a way to decentralize all of the functions listed above, using a mix of peer-to-peer technology, cryptography, probabilities, game theory, physics, and economic incentives. In other words: thanks to the universality of the laws of mathematics and physics, Satoshi was able to build a non-local system.
To be more concrete, let’s have a closer look at these features and how Bitcoin manages to implement them in a decentralized way:
- Account Creation: Thanks to public-key cryptography, user account creation can be completely decentralized. Anyone, at any time, can create one or multiple keypairs to interact with the Bitcoin system. There are no sign-up forms, no central authorities to approve or deny applications, no servers in charge of logins. In essence, creating an account in Bitcoin is just a matter of generating a large random number. You can even flip a coin a couple of times, or roll a pair of dice, as long as you know what you’re doing (and your dice and coin flips are fair).
- Record Ownership: In Bitcoin, every full node has a copy of the ownership records. This radical approach is a simple way to eliminate a centralized registry and optimize for survival: You can’t shut down the registry if everyone is the registry.
- Prove Ownership: Like other systems before it, Bitcoin uses cryptographic signatures to prove ownership. If you have the private key to sign a message, you can prove that the related public key as well as the assets linked to this public key belong to you. No central authority that hands out ownership certificates required.
- Transfer Ownership: Ownership is transferred via a chain of signatures, just like in Hal Finney’s RPOW system. Unlike in RPOW, no central servers are required, since the chain of ownership is hosted (and validated) by every full node.
- Security: Bitcoin is secured in many different ways, all of which rely on cryptography in one form or another, which in turn relies on the power of ridiculously large numbers. The probability that someone will guess your private key or one of your addresses is virtually zero, as is the probability that someone will find the hash of a valid block without doing the necessary brute-force work. The combination of strong cryptography and the cumulative energy expended by miners secures both the assets of users, as well as the integrity of the network. The system itself has never been hacked, making it the most secure computer network of all time. Bitcoin can only be meaningfully attacked at the edges, i.e. private keys can be stolen from individual users or custodians.
- Scarcity: Because Bitcoin is the first practical, non-central solution to the double-spend problem, it made digital scarcity possible for the first time. Satoshi could have chosen any terminal inflation rate, but he chose a terminal inflation rate of zero. The result: 21 million bitcoin, nothing more. What this means for Bitcoin and the world at large will be explored in Chapter 7.
- Controlled Issuance: Because of Bitcoin’s difficulty adjustment, controlled issuance is possible in a decentralized fashion. The difficulty adjustment is what solves the problem of cryptanalytic instability, as Satoshi points out in the whitepaper: “To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour. If they’re generated too fast, the difficulty increases.” During the network’s reward era, which will end approximately in the year 2140, new bitcoins will enter the economy with every valid block, i.e. roughly every ten minutes. Bitcoin’s supply was predetermined at its inception, and arguably, this is the most valuable property of Bitcoin. No other asset in existence has what Bitcoin has: an unchanging supply schedule that can not be argued with.
In short, mathematics allows for the decentralization of all the essential functions of the system and the laws of thermodynamics allow for strong security guarantees. Further, economic incentives and game theory are the glue that keeps everything together.
The result is a distributed system with no single point of failure. Users hold the crypto keys to their own money and transact directly with each other, with the help of the P2P network to check for double-spending.
Satoshi also realized that the only real-world asset that can be linked to a computer system in a trustless manner is energy, nothing else. Every other thing—no matter if it’s gold, paper certificates, real estate, or strawberries, re-introduces a trusted third party because of the inherent disconnect between the digital and the physical world. Someone has to make sure that the real-world assets and the digital representation of these assets—in essence, a list of things—remains up-to-date and in sync. This is what is known as the oracle problem, and proof-of-work solves it in an ingenious, roundabout way: by using energy, and thus physics, as the base truth. One can also think of the oracle problem as a variant of the GIGO principle: Garbage In, Garbage Out. You have to trust whoever is keeping the records that the records are correct. Phrased differently: you can never be sure that the data at hand represents reality, except if the reality is rooted in computation itself.
A Most Timely Idea
You can’t crush ideas by suppressing them. You can only crush them by ignoring them. By refusing to think, refusing to change. And that’s precisely what our society is doing!
Ursula K. Le Guin
As we can see by examining Bitcoin’s pre-history, double-spending and digital scarcity aren’t easy problems to solve. Satoshi’s breakthrough was to find a way to solve both of these problems practically, not academically. The first is solved by a globally shared timechain that is kept in sync via a competitive lottery, the second is solved by the difficulty adjustment as well as the block reward halving. Bitcoin uses the best ideas of its predecessors (digital signatures, reusable proof-of-work, peer-to-peer networks) and combines them in an ingenious way to create something completely new: a decentralized system without a single point of failure.
No single part of Bitcoin can be removed without destroying the whole. Without the timechain, there wouldn’t be a decentralized way to check for double-spending. Without the block reward halving, the bitcoin supply would expand indefinitely. Without the difficulty adjustment, the mining algorithm wouldn’t have cryptanalytic stability, making it trivial for miners to produce bitcoin more quickly. Many cypherpunks dreamed of digital cash. Satoshi took this idea further than anyone else before him, implementing a system that is virtually unstoppable. No matter what happens in the coming decades, the cat is out of the bag, and everyone will have to adjust to a world in which Bitcoin exists.
Bitcoin is an idea whose time has come. As more and more people, companies, and even nation-states move towards a Bitcoin Standard, the unstoppable gravity of Satoshi’s idea becomes ever more apparent. By implementing his idea, he proved that a practical solution to the problems that plagued digital money for decades — double-spending and digital scarcity — is possible. Releasing his software into the wild set in motion a multi-decade process that is driven by an extremely powerful incentive structure. An unstoppable idea, embodied in code. It is this incentive structure that drives Bitcoin’s survival. And with every passing day that Bitcoin refuses to die, humanity is one step closer to freeing money from the capture of the state. It will take some time for the world to come to grips with this most powerful idea. Amusingly, time is also the reason why Bitcoin works in the first place since the main insight Satoshi had is how to keep the time in a decentralized system. Many people thought that this problem was insoluble. Turns out that all that was missing was the right idea.
The name cypherpunk is a playful combination of the words cipher (an algorithm that encrypts and/or decrypts a message) and cyberpunk (a science fiction subgenre spawned by the works of authors like Philip K. Dick, William Gibson, Ridley Scott, and many others). ↩
Internet Assigned Numbers Authority ↩
Timothy C. May, The Crypto Anarchist Manifesto ↩
Diffie and Hellman, 1976, New directions in cryptography (IEEE, PDF) ↩
Rivest, Shamir, Adleman, 1978, A method for obtaining digital signatures and public-key cryptosystems (ACM, PDF) ↩
“The hashcash CPU cost-function computes a token which can be used as a proof-of-work.” http://www.hashcash.org/papers/hashcash.pdf ↩
Hal Finney, RPOW Theory ↩
You can try this yourself using various online tools (e.g. DuckDuckGo) or by typing the following into a command line:
echo -n 1:20:040806:foo::65f460d0726f420d:13a6b8 | sha1sum↩In some of his very early writings, e.g. this README file, Satoshi wrote Bitcoin as “BitCoin”, indicating that it was meant to be understood as two separate words. ↩
From the bit gold early incomplete whitepaper in which Szabo introduces the concept of unforgeable costly assets, linking the scarcity of certain goods to the costliness of their creation. ↩
See his writings on Intrapolynomial Cryptography ↩
MicroMint was one of two micropayment schemes proposed by Ronald L. Rivest and Adi Shamir (the R and S in RSA). The second scheme was called PayWord. Both focused on efficient payments of very small amounts, extending previous works such as Millicent by Glassman et al. Again the idea is to use public-key cryptography and hashes in a clever way to produce coins: “A coin is a bit-string whose validity can be easily checked by anyone, but which is hard to produce. ↩
https://nakamotoinstitute.org/finney/rpow/index.html—See also Shelling Out: The Origins of Money ↩
https://nakamotoinstitute.org/finney/rpow/slides/slide010.html ↩
The Onion Router, torproject.org ↩
Translations
- 🔗 Chinese translation by BTCStudy
- 🔗 Korean translation by Elena
- 🔗 Spanish translation by Entropy
- 🔗 Italian translation by Filippo
- 🔗 German translation by Karl Klawatsch
- 🔗 Malay translation by Linuzri
- 🔗 Spanish translation by Rai Pow
- 🔗 German translation by Rene
- 🎧 German audio by Rob
- 🔗 Russian translation by Tony
- 🎧 Russian audio by Tony
Want to help? Add a translation!
Conversations
- 2022-03-15 ⭐ Was Bitcoin Bringt #7
on Bitcoin’s History, essence, and the necessity of proof-of-work, hosted by Niko Jilch (🇦🇹)
🧡
Found this valuable? Can't support me directly?Consider sharing it, translating it, or remixing it in another way.